CSRF attacks can make your site vulnerable in front of malicious users. They are dangerous as when your sensitive data is lost, your business prosperity is under the threat. That’s why store owners should be aware about what CSRF attack is, how to prevent it and what to do if a possible CSRF attack has been already detected. This post gathers the common cases encountered by the CS-Cart users and the recognized methods to treating possible CSRF attack messages.
What is CSRF?
Cross-Site Reference Forgery, XSRF, “Sea Surf”, Session Riding, Hostile Linking or One-Click attack (as referred to by Microsoft). The names can be different but in general a CSRF attack is a sort of activity designed to trick the victim into sending a malicious request. The attacker gets the identity and privileges of the victim to run an undesired function on behalf of the victim.
The fact is that the browser automatically includes the user credentials associated with the site (session cookie, IP address, Windows domain credentials, etc.). When a user is authenticated to the site, the site does not make a difference between the forged request sent by the victim and a legitimate request sent by the user.
Any functionality that causes a state change on the server is potentially vulnerable to the CSRF attack. The examples of such state-changing functionalities can be:
- Change of the victim’s email address;
- Change of password;
- Purchasing something or transferring funds.
With the use of social engineering (the attacker can send a malicious link via email or chat), an attacker deceives the user to execute the desired action.
For administrative accounts, a successful CSRF might end with compromising the entire web application.
Why do CSRF attacks happen?
CSRF attacks are feasible because web apps trust the cookies sent by web browsers via an HTTP request. The attacker manipulates the victim’s browser to make a request resulting in a change of the server state, a state which is beneficial to the attacker (like transferring funds, for example).
How to prevent CSRF attacks?
An attacker can execute a CSRF attack when he knows which parameters and value combination were used in a form. Adding an additional parameter containing a value unknown to the attacker, but allowing its validation by the server, can help you avoid CSRF attacks.
Administrative accounts like banks or eCommerce merchants need to transition from cookies that perform session-tracking to session tokens that are dynamically generated. These actions will make holding the client’s session more difficult for an attacker.
How do tokens work?
A token or a CSRF Protection Token also known as a Synchronizer Token, works as follows: the client requests an HTML page that contains a form with the user credentials. After the user submits the form, the client sends the tokens back to the server. At this, cookie tokens are sent as cookies, and form tokens are sent as part of the form data.
How to fix an invalid CSRF protection token?
If a token has been compromised, you still can fix it. To do that:
- Open the Chrome settings;
- Click on Advanced on the bottom of the page;
- Click on the Content Settings in the Privacy and Security section;
- Press Cookies;
- Click Add next to Allow;
- Seek for todoist under All cookies and Site data. Delete all Todoist-related entries.
What do CS-Cart users say about CSRF attacks?
Here is what users say on the CS-Cart forum about how they encountered the error message:
Just tried to edit the name of a filter (in this case ‘Designer’). When I clicked Save & Close I received the following error message – Error Access Denied: Possible CSRF Attack Detected – in the top right. It was in the CS-Cart box that usually displays ‘upgrade available’ etc.
When I select either Theme Editor or Edit content on site in Design – Themes, I get an error popup message “Error access denied: Possible CSRF attack” and can’t access these two facilities. (…) Whilst they (hosts) were checking, they also upped the PHP version from 5.6 to 7.1 to speed things up, but I am still getting the CSRF error when selecting either Theme Editor or Edit content on site in Design – Themes.
One of my customers told me that he got the “ErrorAccess denied: Potential CSRF attack detected” message on trying to make an order. What is the cause and the solution to prevent this from happening again?
I’ve just installed trial version for client to try before purchasing, but receiving the following error when trying to upload a banner: Access denied: Possible CSRF attack
I have been in the process of setting up more products for my website. I have had no such errors previously. When updating some pictures for the “option combination” tab, it takes me back to my dashboard and has this message in red “ErrorAccess denied: Possible CSRF attack”. Anyone know this came up all of a sudden, and how to get rid of it?
I am having a huge problem with product option add. I have added 60 variants on a single option, although there are 60 more to add. But couldn’t add anymore because after I hit the “SAVE” button, it redirects to the dashboard and says “Action Denied : POSSIBLE CSRF ATTACK”.
I have enabled/disabled the anti_csrf variable true/false but in any case it is not working.
Maybe you have some restrictions on your server.
After I updated CS-Cart to version 4.3.4, I received an error Access denied: Possible CSRF attack, when I try to move some items from one category to another.
Before I was moving more than 100 products at the same time, but now I receive this error when I move 30 products.
I encountered the error Access Denied: CSRF Attack Possible” when I tried to log in to my cart admin panel.
Since upgrading to 4.11.5 if I try to do a bulk packing slip print. It opens the new window, but then takes me to the Dashboard and gives me the Error “Access denied: Possible CSRF attack”. I’ve cleared cache, logged out, restarted browser, etc. to no avail.
We are trying to change shipping settings for a certain shipping method on our CS-Cart backend but it results in the “errorAccess denied: Possible CSRF attack” message.
My customer can’t log in getting Denied: CSRF Attack. He is getting a message DENIED CSRF ATTACK using Internet Explorer trying to log in.
Reasons behind CSRF attack messages encountered by the CS-Cart users
The most common reason for a CSRF-attack message appearing in the CS-Cart projects is the value of the max_input_vars PHP directive on the server. The server truncates the request and if the security_hash` parameter gets truncated, the error message appears.
How to fix CSRF attack messages?
- If you have a VPS or dedicated server you should check the value of max_post_size and max_input_vars. Increase both of them until you no longer see that error. The same settings are applicable to shared hosting but they are under control of the hosting provider. Ask the host to change them and if they won’t – hop to another host.
- If you do not have access to the settings, create a php.ini file and adjust there.
The values should be as follows:
- upload_max_filesize = 10M
- post_max_size = 10M
- max_input_vars = 10000
You can add php_value max_input_vars 1000 to .htaccess file. To verify that the new setting is active, create a PHP test file that contains the following code in the root directory of your store:
<?php phpinfo();
Also you can find max_input_vars in php.ini file and change the value.
- Try clearing the cookies for your site. CSRF messages are triggered when the session keys don’t match the cookies.
After you clean cookies, you can also try incognito mode in Chrome or Private Window in IE/Edge.
- Sometimes, the Access denied: Possible CSRF attack message appears when your customers bookmark a URL that expects a SESSION key instead of the homepage of the site where a SESSION key is generated. In this case, customers should replace their bookmarks with the homepage URL.
Debriefing some of the remedies against CSRF errors
Increasing the value of the max_input_vars PHP directive to 10000 or more.
The most common way to get rid of that kind of message and fix the problem is to increase the max_input_vars. The max_input_vars directive helps the web application truncate the request. In that case, when the attacker tries to send a big request to your CS-Cart project, it can crash or take down your webserver (DoS attack).
By default, this PHP directive is set to 1000. 1000 means one thousand form fields sent in one request. You cannot send more if such limitation is set. Customers on our hosting benefit from a 5000 value and we bear all the risks of such an increase.
Increasing the max_input_vars directive is a dangerous modification. And if you do change this directive to 10000 or 20000 on your own, we recommend rolling back this modification or refer to your host.
Disabling anti_csrf
You can disable the anti_csrf tweak at the config.local.php file as shown below:
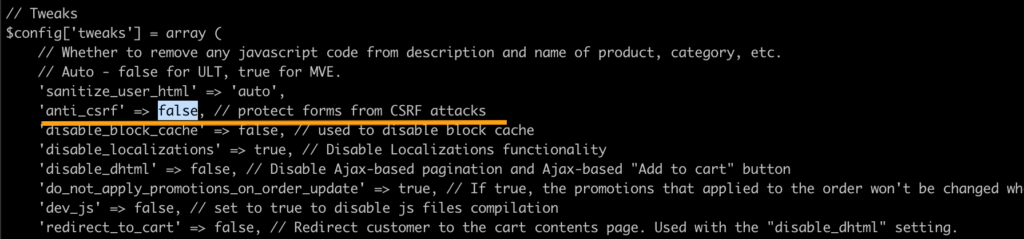
Although, we do NOT recommend this remedy as there are more secure approaches, in most cases, this protection is enough.
Closing
CSRF attacks can ruin your business making sensitive data available to attackers and shutting down the work of the whole application. Our hosting team has a huge experience with sorting out this kind of problems, making tweaks in a safe and efficient way to reinforce your eCommerce project.
