Security is important for any business. And information security is critical if you have a website, especially if you have an online store with customer data. Most of our readers use solutions built on CS-Cart and Multi-Vendor. Today we will talk about how we make our clients’ projects and CS-Cart core safer.
Every system is hackable
There are no 100% secure systems and companies – absolutely everything can be hacked. It is just the matter of time and money to hack a more secure system.
Anyone who thinks that security products alone offer true security is settling for the illusion of security.
“The Art of Deception”, Kevin D. Mitnick
Note that in order to maintain the safety of the project as a whole, it is necessary to monitor and check for safety:
- The very core of the CMS (CS-Cart or Multi-Vendor in our case)
- Changes made to the core of the system by developers
- Add-ons
- Third-party themes and their updates
- Additional integrations and scripts
- Configuration of the server and its components
A mistake or oversight in any of the above points can potentially lead to a disclosure of sensitive and critical project data or even compromise it. In this post, we will tell you how our team helped make the core of CS-Cart safer. The next posts will cover each point individually.
Continuous Security as a CI process
During each release of a new version of CS-Cart and Multi-Vendor (starting from version 4.12.0), we conduct testing to identify information security issues. After completing the Static application security testing (SAST), we launch Dynamic application security testing (DAST). Once all the tests are done, our cyber security specialist analyzes the test results and proceeds to manual analysis. He manually compares the results, checking and confirming the problems or marking them as false-positive.
This set of continuous tests and studies helps make sure that vulnerabilities are not overlooked in customer projects. That is how we maintain overall security.
After a vulnerability or some other problem is confirmed, we study the root cause. We analyze the application code that relates to this problem, regardless of who the developer is. Sometimes, concerns reside within third-party libraries and we inform their developers. We form a set of patches to fix or mitigate the risk of vulnerability exploitation.
When a vulnerability is confirmed, we know how to reproduce it. What is required? To classify the problem. We use the OWASP framework to identify, STRIDE to classify, and DREAD to rate, compare, and prioritize.
Then, we connect with the CS-Cart team via a secure channel. We discuss the plan of action to fix the vulnerability and, if necessary, the plan of information disclosure, to follow them further.
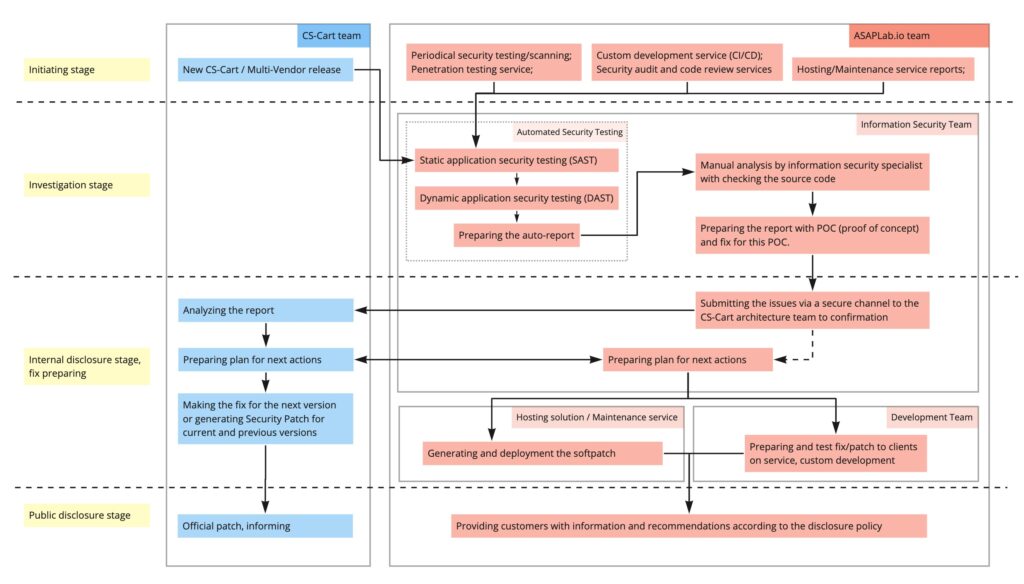
One topic here should be addressed separately. If a vulnerability is critical or we understand that there is a risk to exploit it, we contact our customers and help them apply patches or schedule a fix.
Result
Over the past two months, we have identified and helped fix 7 vulnerabilities in CS-Cart (including, the core and default add-ons) at different severity levels.
We continue our research of security gaps further and commit ourselves to introduce this practice in all future releases of CS-Cart and Multi-Vendor. We plan to implement security testing for third-party add-ons and themes.
ASAP Lab LTD is a partner of Simtech Development for server and project information security and performance optimization.
